If you are an Admin User who wish to create App Passwords so that you can use them in your code/web applications so that you don’t have to store credentials in your application? Example: Azure Function you are developing shouldn’t store the password of the User.
At times, you must’ve noticed that why you can’t create App Passwords even when you are having MFA enabled for yourself!
Here’s why –
Scenario
Let’s say the users are logged in and they go to their Office 365 Account where they can add multiple Authentication Methods. Shortcut for that is https://mysignins.microsoft.com/security-info
- Once they are in Security Info in order to add new method of Authentication as below
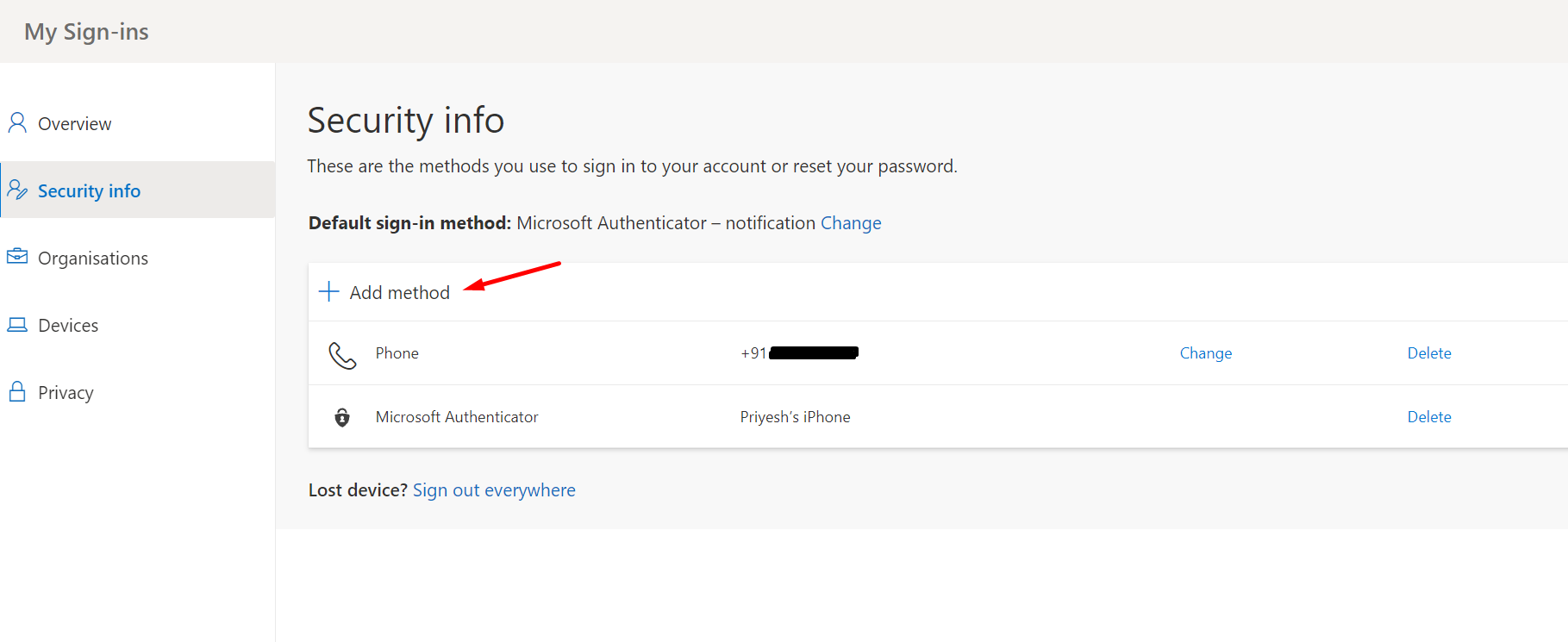
- And they don’t get to create an App Password by default.
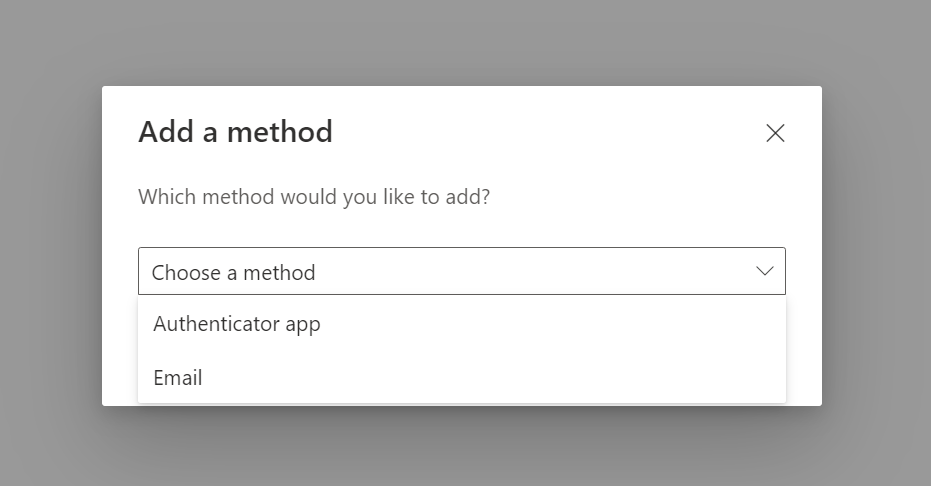
Let’s enable users to be able to create their own App Passwords from Azure Portal.
Enforce Users to use MFA
Let’s say the Conditional Access above is already set. Now, you need to enforce users to use MFA.
- In O365, go to the User in Active User whom you want to allow creation of Azure App Passwords.

Select the user and click on Multi-factor Authentication. - Now, in the multi-factor authentication page, you’ll see the users as whether they are using MFA or not.
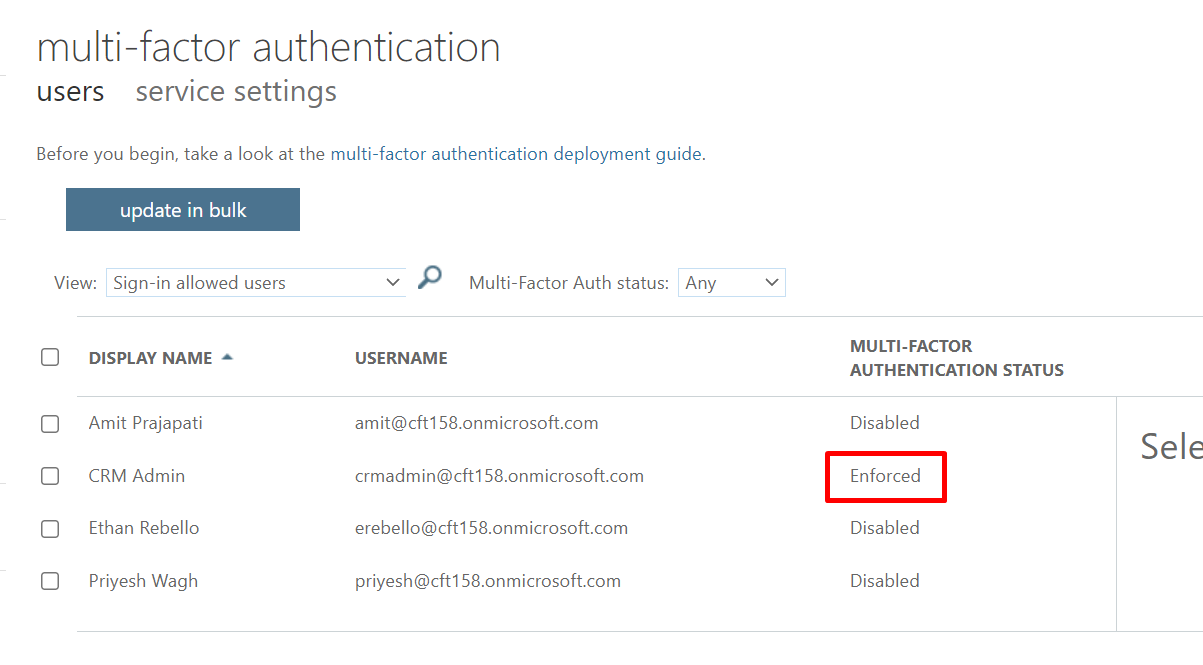
As you see below, CRM Admin is Enabled for Multi-Factor Authentication, but not Enforced.
So, you have to click on Enforce button to enforce the MFA.
But sometimes you don't see enforce option event though default security option enabled on conditional policy in Azure which means user never configure MFA though it's enabled for user. So, you need to configure the MFA first and then comeback and enable enforce and then you will be able to see the app password option in user's security info under personal setting.
MFA Status
Enabled:
User has MFA enabled but have not registered. Meaning if the user has had MFA enabled for 14 days or more, they will be required to register on next login. They will only be prompted/required to register is they login through the web, or setup a new device.
I've had a user Enabled for a year, they worked fine that whole year using Outlook on their computer and phone, as well as Teams. They got a new phone and went to setup Teams on it, at that point they needed to sign in, which required the MFA registration to be completed.
The other issue with this status, is that if an attacker gets their 365 credentials and goes to n login, the attacker will be prompted to register MFA and can use their own device and info, bypassing MFA. There are two ways we know to avoid this. One option is running a PowerShell command to logout all sessions, forcing them to sign back in and register MFA. This command can be ran against the entire organization, or per user. The other option is using a condition access policy to flat out block access to a user or group of users, we have a writeup on that here Block Access | Any Location | Excluding "MFA Trusted IPs , this option requires at least one AzureAD Premium P1 license.
Enforced: User has registered for MFA.
Enabled via Conditional Access: This status will only appear in the Excel report and shows that the user status is "Enabled" through Security Defaults. To confirm an "Enforced" status in this scenario. Check the report columns for "Activation" and "DefaultMFAMethod", the Activation should show "Yes" for Enforced/Registered.
- Now, when you click on Enforce, you’ll see the below message.

- After enforcing, you’ll get a success message as below.
- Once enforced, you’ll see the below status is updated on whoever this is enforced on.
Create App Passwords from My Sign-ins page
Now that we have enforced the User to use MFA, here’s how you can create App Passwords
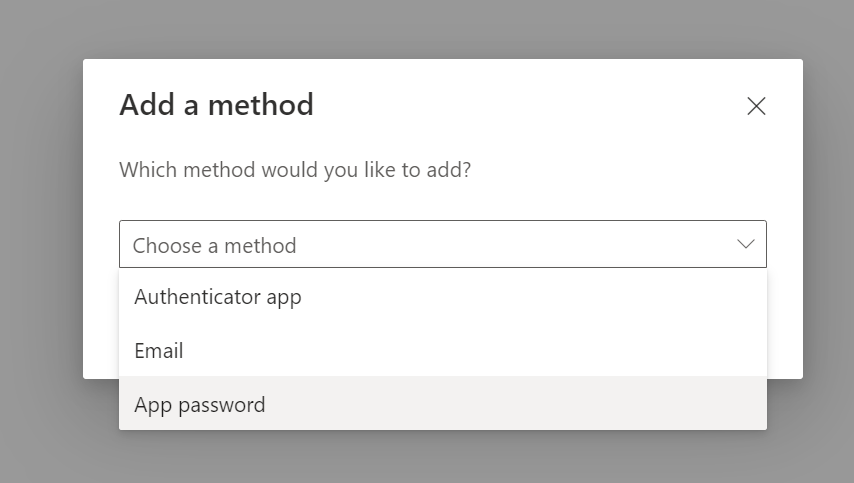
- As shown in the beginning, try to Add a new method

- This time, you’ll be able to see App Passwords as an option to select. Select it and click on Add

- Next, you can give a name to the App Password you are setting. You can give it a suitable name keeping in mind the purpose of the App Password you are creating.

I’ll just give a sample name here since I want to use it in Azure Functions which I’m working on.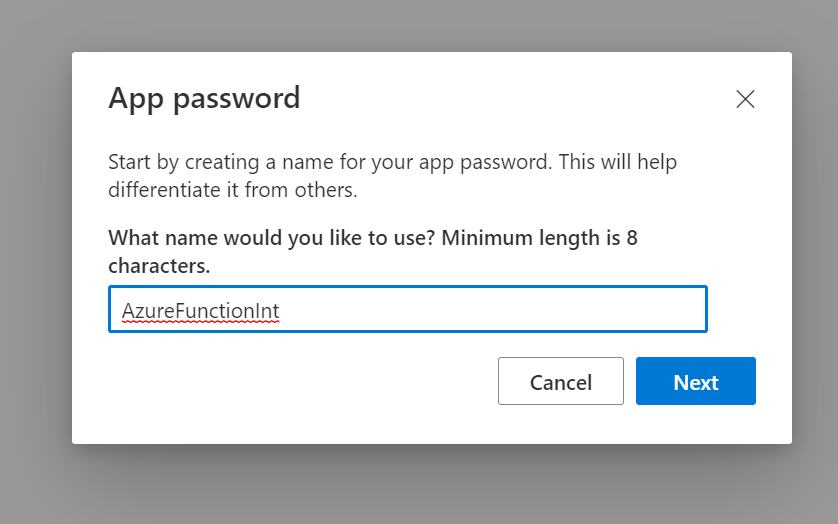
- And once it is created in a few moments, make sure you copy it before clicking on Done. Else, you can’t retrieve this later and it will be created without you noting it down.

- And it’ll be listed among other authentications methods.

Additionally, it is recommended to also review setting up Conditional Access policies too while setting up Azure AD Multi-Factor Authentication – https://docs.microsoft.com/en-us/azure/active-directory/authentication/tutorial-enable-azure-mfa?WT.mc_id=DX-MVP-5003911


